In the ever-expanding digital landscape, web applications serve as the backbone of our online experience. However, their ubiquity also invites a myriad of cyber threats. Web application vulnerabilities, the Achilles’ heel of this technological advancement, pose significant risks to data security and user privacy.
Defining Web Application Vulnerabilities
Common web application vulnerabilities are essentially weaknesses or loopholes within the architecture, coding, or configuration. These flaws, if exploited, can lead to unauthorized access, data breaches, and even compromise the overall integrity of an application.
Understanding these vulnerabilities requires a nuanced perspective. It involves recognizing that the very features that make web applications dynamic and interactive can inadvertently create opportunities for exploitation as well as create a scalable web application itself. As users interact with web applications through input fields, databases, and interconnected components, a delicate balance exists between functionality and security vulnerabilities in web applications. Any lapse in this balance can pave the way for malicious actors to exploit vulnerabilities.
Diverse Faces of Vulnerabilities
They come in various forms, each presenting a unique challenge to the security of web applications. From SQL injection, where attackers manipulate databases, to Cross-Site Scripting (XSS), enabling the injection of malicious scripts into web pages, the threat landscape is both vast and intricate.
Consider SQL injection, for instance. This vulnerability arises when an application fails to properly validate and sanitize user inputs before processing them in SQL queries. Attackers can then insert malicious SQL code, potentially gaining unauthorized access to sensitive databases. Similarly, Cross-Site Scripting involves injecting scripts into web pages viewed by other users, allowing attackers to steal session information or compromise user data.
As technology evolves, so do the tactics of malicious actors. Web application vulnerabilities extend beyond the traditional suspects, with emerging threats like API-related vulnerabilities and serverless application risks adding new layers of complexity to the security landscape.
Implications of Exploitation
The consequences of successfully exploiting these vulnerabilities extend beyond the digital realm. Financial losses, reputational damage, and legal consequences loom large, underscoring the importance of a proactive and comprehensive approach to web application security.
Financial losses can manifest in various forms, from direct theft of funds to the costs associated with remediation and system restoration. Moreover, the reputational damage resulting from a data breach or a compromised application can erode the trust of users and partners, impacting an organization’s credibility in the long term.
Legal consequences, especially in the era of stringent data protection regulations, can be severe. Non-compliance with laws such as the General Data Protection Regulation (GDPR) can lead to substantial fines, further emphasizing the need for organizations to prioritize robust security measures.
Navigating the Complex Terrain
This process requires a deep understanding of common flaws, their potential impacts, and the strategies to mitigate these risks. In the subsequent exploration, we will delve into specific types of web app vulnerabilities and delve into effective mitigation strategies, offering a roadmap for fortifying applications against potential cyber threats.
As we embark on this journey, we must recognize that web application security is not a one-size-fits-all endeavor. It demands a continuous commitment to staying informed about emerging threats, implementing best practices, and conducting regular security audits and testing.
In the upcoming sections, we will unravel the intricacies of SQL injection, Cross-Site Scripting, and other web application security vulnerabilities, shedding light on the mechanics behind each threat. Additionally, we will explore mitigation strategies, emphasizing the proactive measures organizations can adopt to secure their web applications and protect the sensitive data entrusted to them.
Common Vulnerabilities in Web Applications Explained
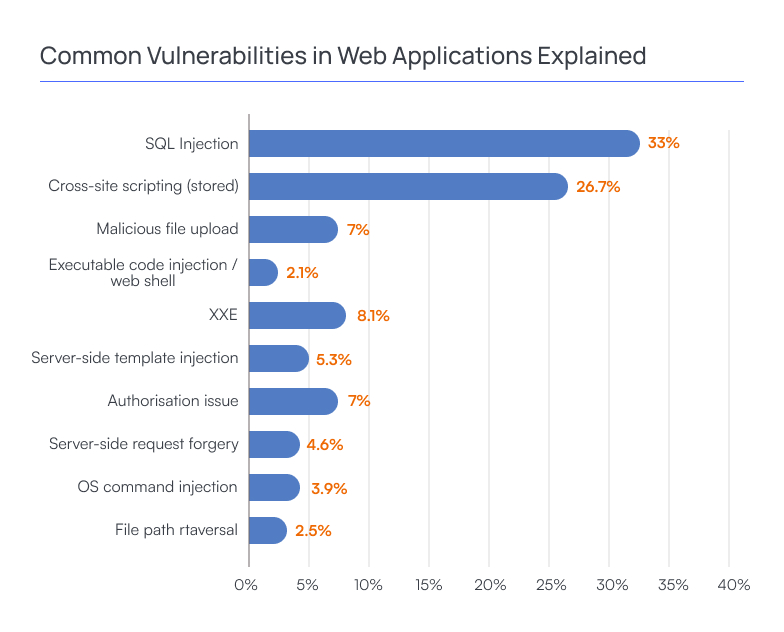
Injection Attacks
Injection attacks, a persistent menace in the digital landscape, occur when malicious code is injected into input fields, exploiting vulnerabilities in an application’s processing mechanism. SQL injection (SQLi) and Cross-Site Scripting (XSS) are notable examples.
Mitigating injection attacks involves implementing parameterized queries to thwart SQL injection attempts and employing output encoding to prevent the execution of injected scripts in the case of XSS.
Data Leakage

These common vulnerabilities in web applications pose a substantial risk, leading to unauthorized access and exposure to sensitive information. This can occur through insecure data storage, transmission, or inadequate access controls.
To address data leakage, encryption of sensitive data in transit and at rest is crucial. Implementing strong access controls, conducting regular security audits, and ensuring data minimization practices can further enhance data protection.
Security Misconfigurations
Security misconfigurations arise when web applications are not properly configured, leaving unintended access points open to attackers. Default credentials, unnecessary services, and overly permissive approvals are common culprits in misconfigurations.
Preventing security misconfigurations involves conducting regular audits of application settings, removing unnecessary services, and employing the principle of least privilege. Automated tools can assist in identifying and rectifying misconfigurations, ensuring a more robust security posture.
Broken Access Control
Broken access control vulnerabilities occur when an application fails to enforce proper restrictions on user access, allowing unauthorized users to perform actions or access sensitive data.
Mitigating broken access control involves implementing proper authentication mechanisms, authorization checks, and role-based access controls. Regularly reviewing and testing access controls can identify and address potential vulnerabilities.
Broken Authentication
Broken authentication vulnerabilities arise from weaknesses in user confirmation processes, potentially leading to unauthorized access. Common issues include weak password policies, session management flaws, and inadequate protection of authentication credentials.
To enhance security, implement multi-factor authentication, enforce strong password policies, and regularly update confirmation mechanisms. Monitoring for unusual login activity can also help identify and respond to potential breaches.
Cross-Site Scripting (XSS)
XSS application security vulnerabilities enable attackers to inject malicious scripts into web pages viewed by other users, compromising user data or session information.
Mitigating XSS involves implementing a Content Security Policy (CSP), input validation, and output encoding. Educating developers on secure coding practices and leveraging security frameworks can further reduce the risk of XSS attacks.
Cross-Site Request Forgery (CSRF)
CSRF vulnerabilities enable attackers to trick users into performing unintended actions without their consent. This occurs when an authenticated user unknowingly submits a request initiated by a malicious actor.
Preventing CSRF involves implementing anti-CSRF tokens, validating the origin of requests, and ensuring that sensitive actions require authentication. Educating users about the importance of logging out from web applications and being cautious about clicking on unfamiliar links further enhances protection.
Unverified Redirects and Forwards
Unverified redirects and forwards vulnerabilities occur when an application redirects users to untrusted or malicious sites without proper validation. This can be exploited for phishing attacks or to redirect users to harmful content.
Mitigating this risk involves validating and sanitizing redirect URLs, avoiding user-controlled input in redirects, and implementing secure redirection mechanisms.
Insecure Direct Object References (IDOR)
IDOR vulnerabilities arise when an application provides direct access to objects based on user-supplied input. Attackers can manipulate this input to access unauthorized data or perform actions.
To mitigate IDOR vulnerabilities, implement proper access controls, enforce least privilege principles, and validate user inputs thoroughly. Regularly audit and review access controls to identify and address potential weak points.
Remote File Inclusion (RFI)
RFI vulnerabilities occur when an application includes a file from a remote server without proper validation, potentially allowing attackers to execute arbitrary code.
Mitigating RFI involves validating and sanitizing file inclusions, implementing secure coding practices, and using whitelists to control allowed file paths. Regularly updating and patching software can also help prevent exploitation of known flaws.
In conclusion, a holistic approach to web application security demands a deep understanding of these common web applications security vulnerabilities. By implementing robust mitigation strategies, staying vigilant against emerging threats, and fostering a culture of security awareness, organizations can fortify their web applications against potential exploits and safeguard the sensitive data they handle.
But How to Fight These Obstacles?

Injection Attacks Prevention
- Use parameterized queries to thwart SQL injection attempts.
- Employ stored procedures and prepared statements in database interactions.
- Implement input validation and output encoding to prevent code injection.
Data Leakage Prevention
- Encrypt sensitive data in transit and at rest.
- Implement robust access controls to restrict data access.
- Regularly conduct security audits to identify and address data exposure risks.
Security Misconfigurations Prevention
- Regularly audit application settings and remove unnecessary services.
- Employ the principle of least privilege for user permissions.
- Utilize automated tools to identify and rectify misconfigurations.
Broken Access Control Prevention
- Implement proper authentication mechanisms.
- Enforce role-based access controls.
- Regularly review and test access controls to identify vulnerabilities.
Broken Authentication Prevention
- Implement multi-factor authentication for added security.
- Enforce strong password policies and use secure password hashing.
- Regularly update confirmation mechanisms to address known vulnerabilities.
Cross-Site Scripting (XSS) Prevention
- Implement a Content Security Policy (CSP) to control script execution.
- Conduct input validation and output encoding to mitigate script injection.
- Educate developers on secure coding practices and use security frameworks.
Cross-Site Request Forgery (CSRF) Prevention
- Implement anti-CSRF tokens to validate request origins.
- Ensure that sensitive actions require user authentication.
- Educate users about the risks of CSRF and safe browsing practices.
Unverified Redirects and Forwards Prevention
- Validate and sanitize redirect URLs to prevent malicious redirection.
- Avoid using user-controlled input in redirect mechanisms.
- Implement secure redirection mechanisms to trusted destinations.
Insecure Direct Object References (IDOR) Prevention
- Implement proper access controls to restrict user access.
- Enforce least privilege principles for user permissions.
- Thoroughly validate user-supplied input to prevent unauthorized access.
Remote File Inclusion (RFI) Prevention
- Validate and sanitize file inclusions to prevent arbitrary code execution.
- Implement secure coding practices and avoid dynamic inclusion of files.
- Regularly update and patch software to address known vulnerabilities.
By incorporating these prevention measures, organizations can significantly enhance the security of their web applications, minimizing the risk of exploitation and safeguarding sensitive data from potential threats.
Securing the Digital Realm: Our Perspective on Web Application Vulnerabilities
In the expansive digital landscape, the security of web applications stands as a paramount concern, and Binerals, a trailblazing company in secure web application development, takes center stage in fortifying this critical frontier. This exploration navigates through the intricate world of common flaws, unveiling the nuanced expertise and proactive strategies employed by our company to safeguard web applications from potential exploitation.
Injection Attacks. In the unceasing battle against injection attacks, Binerals harnesses their expertise in secure coding practices. By implementing advanced measures such as parameterized queries and input validation, they fortify applications against the insidious threats of SQL injection and Cross-Site Scripting (XSS). The integration of Content Security Policy (CSP) into Binerals’ web development services approach adds an additional layer of defense against malicious code injection.
Data Leakage. Binerals’ commitment to data security is evident in their multifaceted strategy. Encryption of sensitive data in transit and at rest is ingrained in their development philosophy, ensuring that client information remains impervious to unauthorized access. Rigorous access controls and regular security audits form the backbone of Binerals’ approach, fostering a robust defense against potential data leakage vulnerabilities.
Security Misconfigurations. With an acute awareness of the risks posed by misconfigurations, Binerals employs cutting-edge automated tools to conduct regular audits, eliminating potential weak points. The company adheres to the principle of least privilege, meticulously configuring applications to minimize common vulnerabilities in web applications. Binerals’ proactive stance ensures that unnecessary services are promptly removed, bolstering the security posture of their web applications.
Authentication and Access Control. Multi-factor authentication, robust password policies, and continuous updates to confirmation mechanisms characterize our approach. Binerals’ commitment to proper access controls is exemplified by their implementation of role-based access controls and regular testing protocols, reducing the risk of unauthorized access.
IDOR and Remote File Inclusion. Binerals’ expertise extends to combating Insecure Direct Object References (IDOR) and Remote File Inclusion (RFI). Granular access controls, adherence to least privilege principles, and thorough validation of user inputs form the crux of their defense. Regular software updates, a hallmark of Binerals’ commitment to security, further mitigate the risks posed by these vulnerabilities.
In this intricate landscape, our team emerges as a beacon of expertise and innovation in secure web application development. Through a blend of advanced technologies, proactive strategies, and a relentless commitment to safety, Binerals not only fortifies web applications against common vulnerabilities but sets a standard for excellence in an ever-evolving digital era. As organizations traverse this intricate landscape, Binerals’ name resonates as a trusted partner, guiding the way toward resilient and secure web applications.
FAQ
What are web application vulnerabilities?
Web application vulnerability is a weakness in the design, coding, or configuration that can be exploited, posing risks like unauthorized access or data breaches.How can SQL injection be prevented?
SQL injection can be prevented by using parameterized queries, input validation, and implementing secure coding practices.What measures enhance Cross-Site Scripting (XSS) security?
XSS security is bolstered by implementing Content Security Policy (CSP), input validation, and output encoding to prevent the execution of malicious scripts.How does Broken Authentication impact web applications?
Broken authentication can lead to unauthorized access. Prevent it by enforcing strong password policies, multi-factor authentication, and regular updates to confirmation mechanisms.What is the role of access controls in mitigating vulnerabilities?
Access controls restrict user actions. Regularly reviewing and testing access controls, enforcing the principle of least privilege, and employing role-based access controls enhance fighting the web application security issues.